Kerberos Trust Pipeline and Abuse
Visuals for Kerberos authentication in Active Directory. These are excerpts taken from my Derbycon presentation.
Will add more later :)
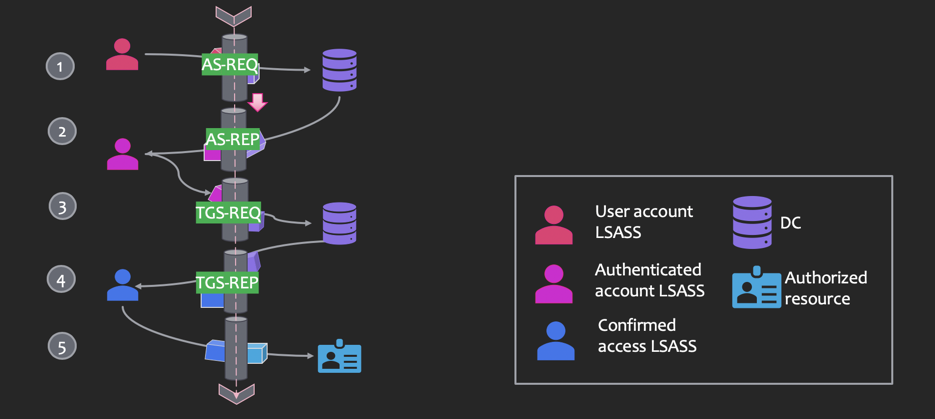
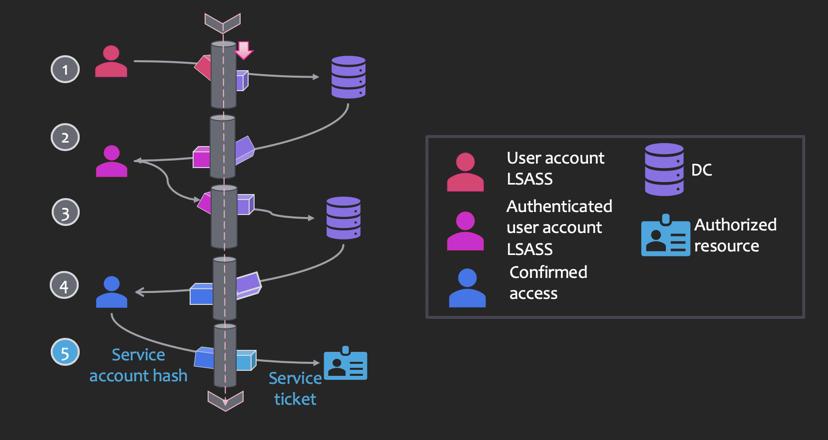
- AS-REQ: authentication service request to a domain controller
- AS-REP: authentication service reply from a DC containing the TGT (if auth successful) encoded/signed by the krbtgt hash
- TGS-REQ: a ticket-granting service ticket request with the user’s TGT
- TGS-REP: a ticket-granting service ticket is sent containing a service ticket
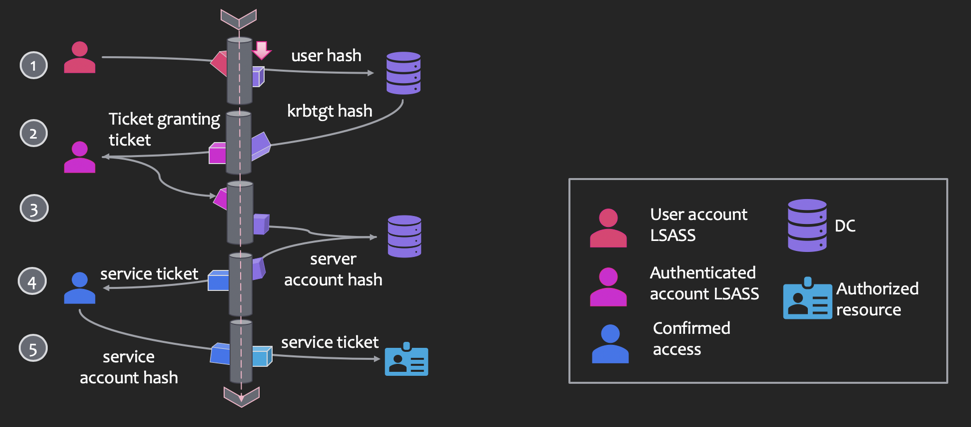
- A user hash is sent to a domain controller (DC)
- Ticket Granting Ticket (aka auth token) is encoded with krbtgt (Kerberos ticket-granting service) hash
- Validated user requests access to computer or resource
- If valid, the DC sends back a service ticket that is encoded with a server hash
- A service ticket for a service or resource is sent with the encoded service account hash
Abuse :)
Overpass-the-Hash
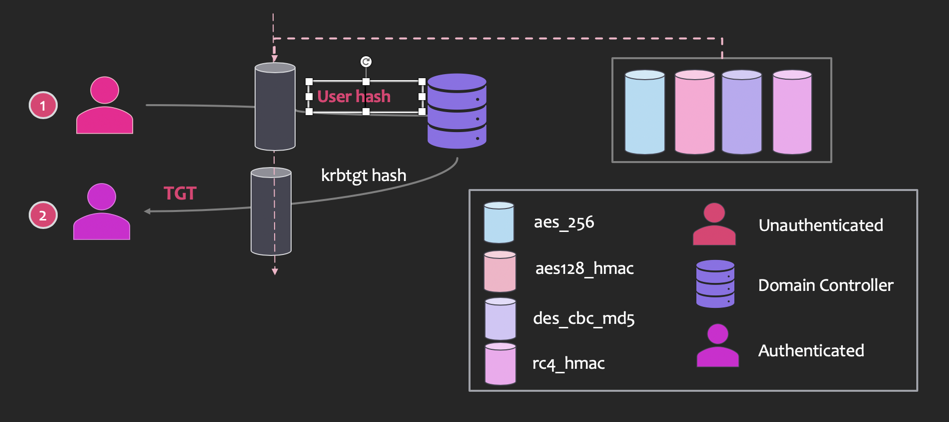
Golden Tickets
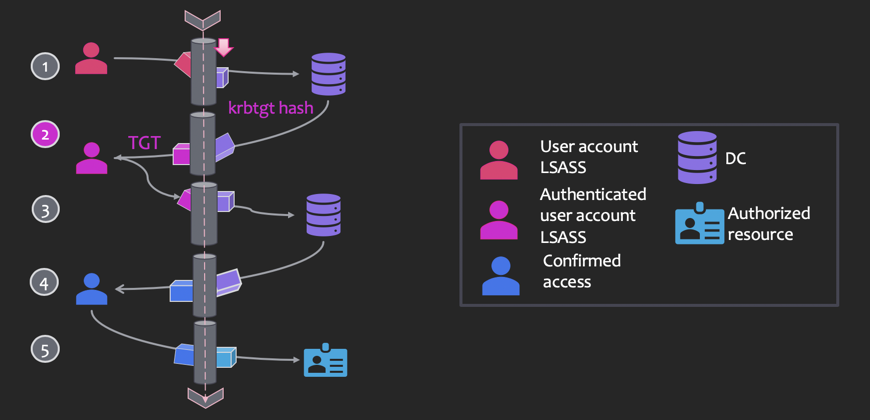

Silver Tickets
Unconstrained delegation
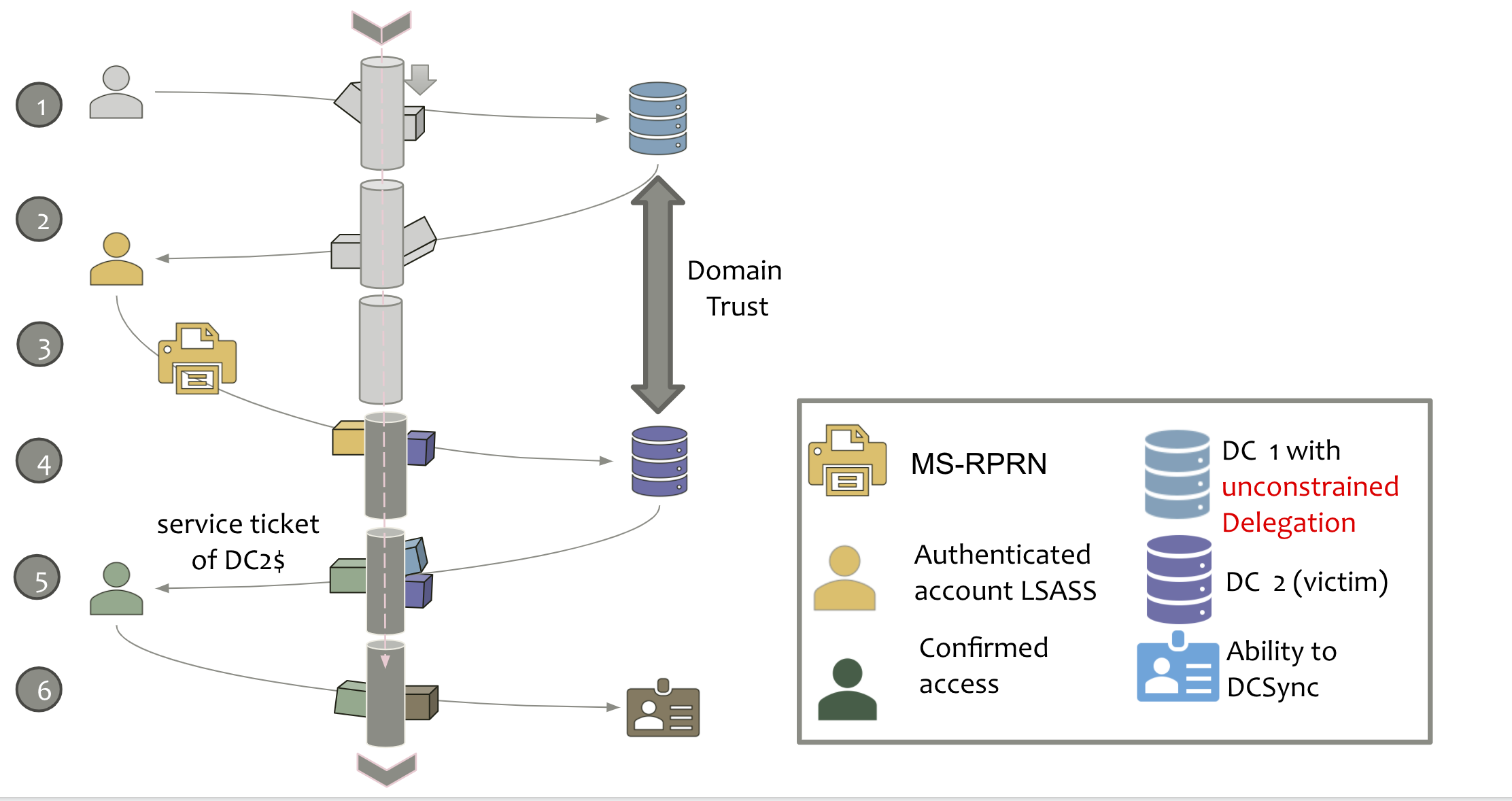
If a server is configured for unconstrained delegation, when a user requests/submits a service ticket for a service on that system:
- The user requests a forwarded TGT (3)
- The forwardable TGT is sent in the authenticator packaged with the service ticket in the AP-REQ to the target service (5)
- The service/system extracts the user’s forwarded TGT and uses it to connect to any service as if they are that user (6)
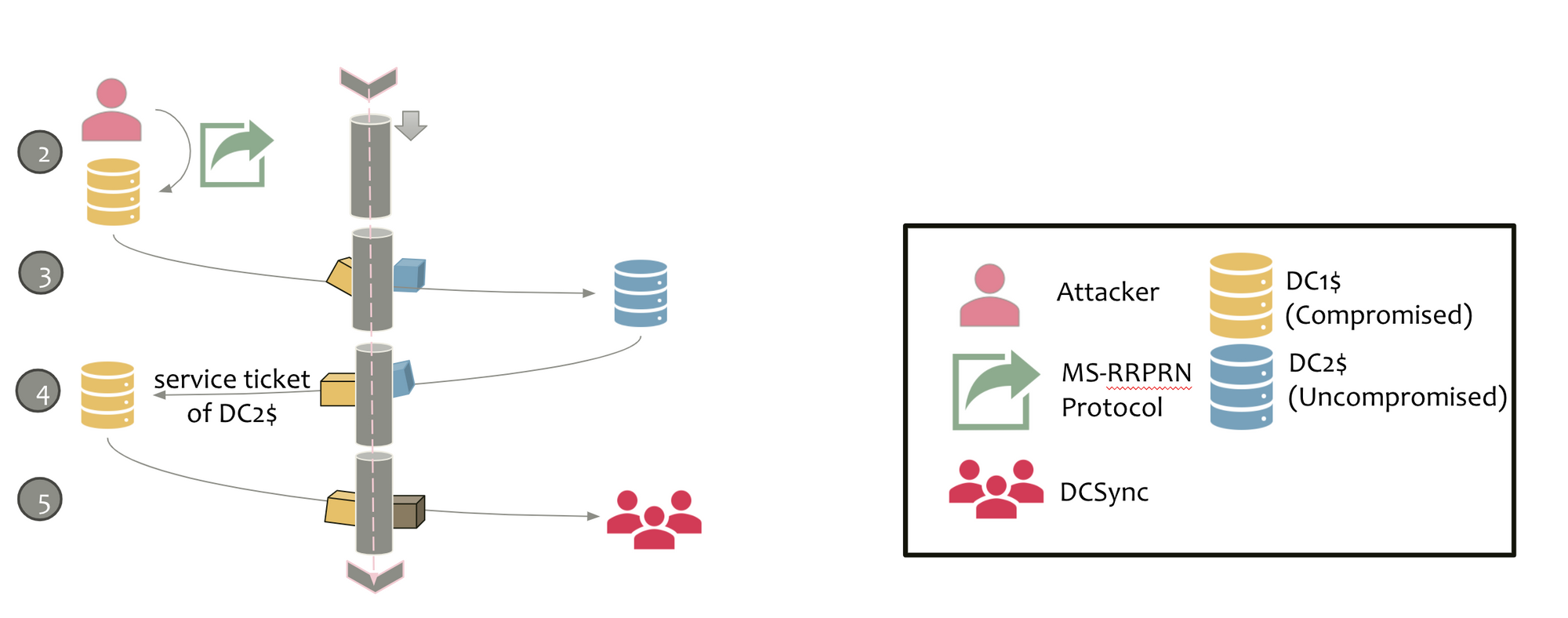
Printer Bug... compromise the entire forest
The “printer bug” from Lee Christensen abuses a legacy old but enabled by default on Windows Print System Remote Protocol (MS RPRN) “feature.
You can coerce any machine in the forest to connect to your unconstrained “capture” server, extracting out the target system’s TGT.
Full deck: https://drive.google.com/file/d/1Q7SPz7cMa1YqMtJT4JoIfoJXECoobcA1/view
