Abusing Bias Part One: Infrastructure
I think about my social engineering skills as a byproduct of living a rebellious life. My friends were busy when I wanted to travel the world, so I went alone. I wanted to go to the best clubs in Miami, so I bypassed security guards. I wanted to break into Fortune 500 companies (legally), so I became a red team operator.
The purpose of this blog series is to highlight similarities between seemingly different fields — red team operations and social engineering. Although this post focuses on the similarities between covert infrastructure and social engineering, the plan is to cover initial access, situational awareness, privilege escalation, and lateral movement in future blog posts. For technical information on how to design, create, monitor, harden, and automate red team infrastructure, please visit @bluescreenofjeff’s blog — Red Team Infrastructure Wiki.
Be who people expect you to be. Create traffic admins expect to see.
As a consultant, I travel often for work, which means lots of potential Uber/Lyft conversations. When drivers ask what I do for a living, I would mention cybersecurity, but if I did that, the conversation would never end. I don’t look like someone who works in cybersecurity, which catches drivers off guard. They always want to know more. I didn’t know if the drivers were talking to me because of my appearance or because they were interested in my role. It doesn’t matter — I wasn’t interested in talking. Instead, I created profiles that are believable yet aren’t particularly conversation worthy, and used those to deflect chatty drivers. I know both roles well — I’ve been to my fair share of Walgreens stores and have a basic understanding of graphic design.
Comfortable attire — Walgreens cashier
Driver : So what’s the craziest thing you’ve seen in a Walgreens?
Me: Well last year a lady walked in, puked on the floor, purchased some Arizona Iced Tea, and slipped in her vomit on her way out. Idk.
Business attire — Graphic designer
Driver: Oh so like you make ads for marketing? What’s your favorite part?
Me: I don’t really do that type of graphic design.
Creating a narrative
The best way to understand how the world sees you in an unbiased way is to talk to Uber and Lyft drivers. Let them narrate your personality and persona for you. I found out that my age is anywhere from 17–28, and this assumption is mostly determined by my clothing.
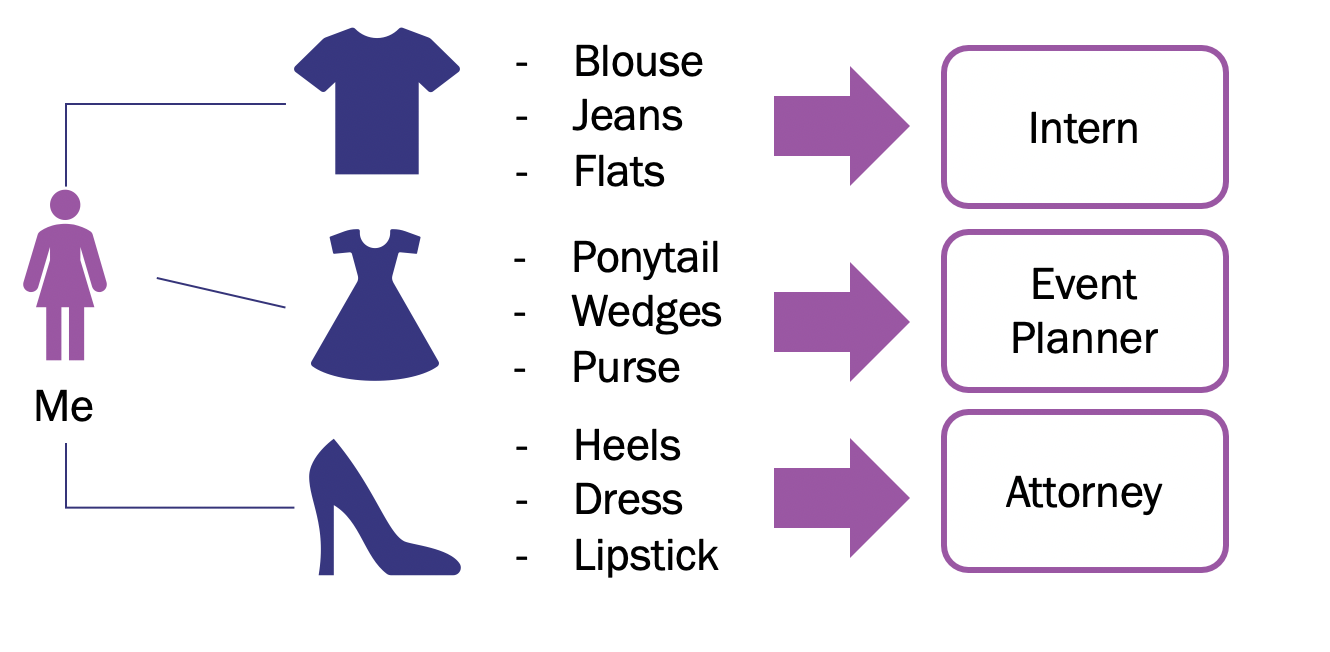
The same principles apply to Cobalt Strike’s beacon, a popular command and control (C2) software. operators create . I won’t be getting into the details of what Cobalt Strike is/isn’t, but to summarize all of Raphael Mudge’ blogs posts, Cobalt Strike is the James Bond of C2 software. It does it all — token manipulation, network discovery, process injection…
This post will only cover how operators use Beacon’s HTTP indicators to emulate threat actors or blend in with network traffic.
Each profile can be entirely customized via Malleable C2 Profiles. With the help of Cobalt Strike’s profile functionality, @Harmj0y (aka Will Schroeder), used the indicators of known malicious activity to model threat actor behavior. By including functionality to control how the traffic is sent and reviewed, an operator creates a narrative with every profile.
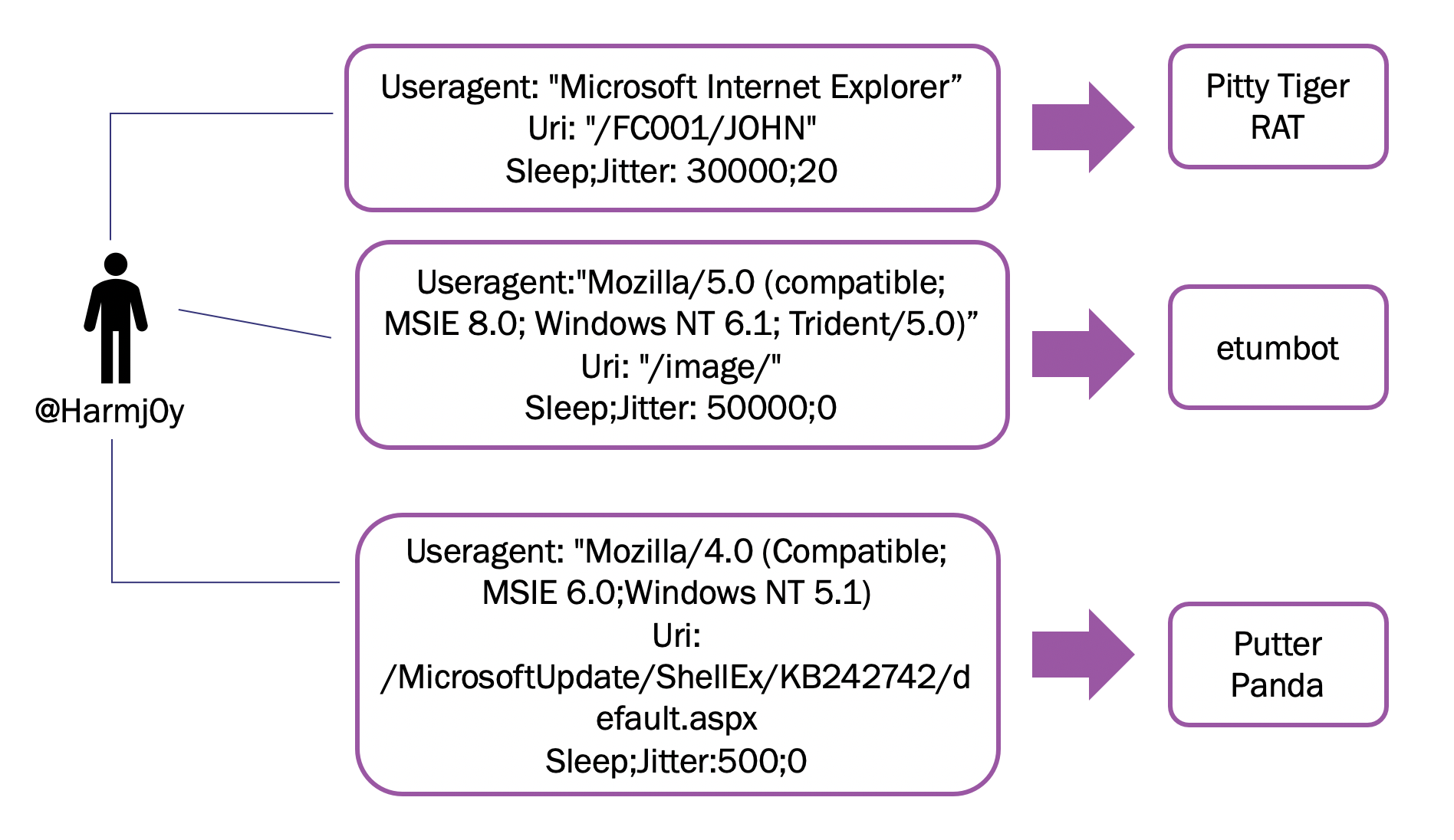
To figure out how much time should be spent developing a narrative and c2 profile, ask yourself:
- How will this be used?
- What is the risk of getting caught?
I use my intern narrative while scoping out buildings or cloning badges because there is a low cost to getting burned, whereas I use my attorney narrative when escalating privileges and accessing restricted areas. Being an intern is easy because interns are assumed to be more or less useless. On the other hand, attorneys are expected to be very knowledgeable and specific about company policies, current litigation, and requests. I need a really unique explanation for why I’m requesting someone to do something unusual.
Same thing with Cobalt Strike profiles. How much time do you have? How will the profile be used? You might be able to get away with using Harmj0y’s classic amazon.profile, but it is more likely to get caught and blocked by defenders. Bluescreenofjeff (aka Jeff Dimock) made a script to help customize Cobalt Strike profiles, but the super stealthy profiles are home grown. Rome wasn’t built in a day, and you can finesse your profiles and narratives over time.
Maturing a narrative with the right indicators
I learned at an early age that telling guys “no” isn’t as effective as “I have a boyfriend.” When traveling alone, I started wearing (fake) wedding rings. Wedding rings deflect many (not all) unwanted advances, and I can be more sure that guys are talking to me because they’re interested in conversation. If a someone asks about my fake fiancé, I tell them:
“Oh yeah he’s at our hotel. He wasn’t feeling great after dinner, but if he’s feeling better he’ll join me.”
I confirm my prior statement confidently, and create a story around why he isn’t here now. This tactic has proven effective for me in many situations. For example, while in Tokyo, I was pulled off the streets and pushed towards a van. I told the man:
“Where am I going? I need to tell my fiancé $Todd… I’m meeting him at a bar. He hung out at the hotel while I was purchasing souvenirs and will be worried if I don’t show up. I mean he could track me on Google maps but he will be so freaked out.”
The man asked about the logistics of when/where I would be meeting $Todd and let me go. I use a wedding ring as a tool to further confirm my narrative and establish credibility. When setting up infrastructure, operators use many tools, such as a free Let’s Encrypt certificate, to add legitimacy to a campaign or website. Instructions for setting up SSL with Let’s Encrypt are here.
Real fiancés wear rings. Real websites use certificates. It doesn’t matter if the ring is $5 from Claire’s or that the certificate is self-signed — it’s an indicator that my story and site are legit.
Operators can confirm their legitimacy and specify how websites handle web traffic with a variety of tools — iptables, socat, apache mod_rewrite, etc. Operators have a lot of control over how a malicious servers handles targets, unintended users, and web bots. Sample rules include the following:
- Allow users from a specific IP address
- Redirect Safari users to a different site
- Block access from web crawling bots
- Restrict access to the malicious payload to one request — all other requests (ie future incident responders triaging the event) will be sent to a 404 page
Legitimacy
Before physically breaking into a building, I do a significant amount of research on the company. I memorize names, job titles (especially department managers), and products and input a few names into my phone. Regardless of my social engineering skills, I may need to provide some type of proof of identification to security guards. When this happens, I take out my phone and dial my $departmentManager, whose contact information includes the name of a real department manager and the phone number of another red team operator. After a co-worker verifies my identity, I’m in the clear. Huzzah!
Bypassing the security guard using a third party is comparable to bypassing web filtering solutions. While setting up phishing domains, operators need to get the phishing domains categorized, which can be done via web filtering vendors. They take the following into consideration:
- Site content (especially headers)
- Length of domain ownership
- Certificates
(A Few) Web Filtering Vendors
Getting domains categorized is necessary for creating covert infrastructure, but doing so does not guarantee that operators will be able get emails to a target’s email inbox. The impact web filtering solutions have on restricting access is similar to that of credit score when purchasing a house. A high credit score is necessary for purchasing a house, but a high credit score does not guarantee that the buyer can purchase the house.
Be real
I studied abroad in the Czech Republic. As an angsty teenager looking to broaden my horizons, I wanted to get a feel for Communism. To do so, I sent out many cringe-worthy emails like this:
“Hello, I’m a study abroad student from the United States looking to learn more about Communism. I’m conducting a research project comparing and contrasting the US and Czech economies, and I would appreciate 15 minutes of your time. Regards.”
While many Czech businessmen did not respond, many replied, and I met with ~ 25% of them. They invited me to their office and we chatted about their thoughts on the strengths and weaknesses of capitalism vs Communism. The businessmen were familiar with students asking for career advice, and they wanted to help. Looking back, I don’t know how I pulled that off or exactly why it worked, but I started using the same approach in my physical assessments. And guess what, it worked! The best way to look like something real is to be something real.
Building real websites
Adobe’s Behance site is intended for designers and creatives to share ideas and collaborate, but I like using it to find phishing templates. I tagged a few of my favorites here: https://www.behance.net/fuzzzynoise/appreciated
Building real resumes
When creating phishing campaigns, don’t overthink it. How would real job seekers create their resumes? How do they create their resume content? Templates!
Familiarity
What matters more…1) a statement is true or whether the person has 2) heard the statement before? … The answer? #2.
Fun Facts:
- The Great Wall of China is not visible from space
- 98.6 F is not the standard for body temperature
- Gum does not stay in your body for 7+ years
Operators also leverage anchoring principles when preparing for an operation by sending unassuming emails to public addresses. Defenders create filtering rules based on known malicious activity, which sometimes includes prior interactions with domains. For example, a rule could be created that restricts traffic from infrequently used domains or requires emails sent from new domains to be reviewed by IT. I have a lot to say about recognition in future blogposts (especially situational awareness), but for now I will focus on the importance of using infrastructure to establish familiarity.
Whether we realize it or not, people make 35,000 decisions a day. We don’t actively deliberate the majority of these decisions, and we can’t. If people thought about the short-term impact, unintentional consequences, decision criteria, etc. for all of our actions, we would be paralyzed by the tsunami of decisions. Instead, people group concepts and ideas.
Similar to sorting algorithms in computer science, grouping increases efficiency and productivity by applying a set of rules across similar objects rather than repeating the same computation for each individual object. While incredibly important to the development and progress of humanity, our tendency to group objects and people is the crux of bigotry and racism, and this “feature” can be exploited in both human interactions and computer networks.
Being an effective social engineer isn’t just being a good liar. Great social engineers leverage bias to anchor ideas into their targets.
Originally published on February 4, 2019 here: https://posts.specterops.io/abusing-bias-part-one-infrastructure-e0ea74652b6e
