The Hitchhiker’s Guide To Initial Access
(Mostly) Harmless
If aliens started monitoring Earth, it would appear that people are good — harmless, in fact. Our civilization rewards generosity, encourages people to contribute to their communities, and emphasizes actions that ‘spark joy.’ But under closer inspection, the aliens would discover disruptive outliers willing to take advantage of altruistic behavior and harm j0y.
This is the second part of a blog series focused on bias (part 1 can be found here), and this post will focus on identifying and applying bias to our everyday interactions and phishing targets. As an avid Douglas Adams fan, I’m using metaphors and truisms from his Hitchhiker’s Guide to the Galaxy series to explain initial access, focusing on phishing.
“The history of every major galactic civilisation tends to pass through three distinct and recognisable phases, those of Survival, Enquiry and Sophistication, otherwise known as the How, Why and Where phases.
For instance, the first phase is characterised by the question How can we eat?, the second by the question Why do we eat?, and the third by the question Where shall we have lunch?” — Douglas Adams
For adversary simulation, this can be translated to:

- Plenty of offensive security teams are hung up on the survival portion — “How can we gain access to a target?” and it leads to a never-ending rabbit hole. At the end of this post, I listed some great resources from researchers who have helped answer this question.
- Enquiry is more nuanced. Why do we gain access to this target? Step away from the keyboard for a few minutes and think about the purpose of phishing and why you are selecting targets. Although there are already strong security philosophers out in the Twitterverse, I believe the industry could use more. I like @RidT and @darkQuassar. If you know others, please let me know :)
- Now, the tricky question — sophistication. Where is the path of least resistance to our objective? To answer this question, operators have to consider the client’s environment…Who could we target?… Everyone? Recruiters? Who should we target?… IT admins? Interns?… We should target people like us.
Hitchhiker’s Guide to Target Selection
When I was in Yosemite, my friend and I overestimated our cardiovascular abilities and couldn’t make it down to the valley before sunset. As we talked through our options, we realized we only had two options:
1) sleep on the ridge or
2) hitch a ride down.
We chose the latter.
Instead of sticking our thumbs out on the side of the road, we walked up to individuals, asked where they are headed, and requested to join. The fastest way to grab a ride would be to ask everyone for help, but we chose to be selective. My friend and I depended on the generosity of strangers, but we were confident someone would give us a ride.
It’s human nature to be helpful. According to Ichiro Kishimi in The Courage to be Disliked, helping others and feeling part of a community is the secret to happiness.
We targeted families because we assumed the chance of a family being creepy is lower than the total population. Without realizing it, we created a risk tolerance ratio and rated each parking lot dweller against it. We stereotyped, leveraged our bias, and selected people that looked like they wouldn’t kidnap us. As minutes went by, our risk tolerance increased, and we became increasingly open to approaching less than ideal candidates.
Throughout an operation, operators constantly assess their risk tolerance and where they are in the engagement. As time goes by, operators’ risk tolerance increases… aka they can send riskier phishing campaigns.
Targeted Hitchhiking

We had a few (or many) rejections, but eventually a father/daughter pair from Frankfurt, Germany agreed to drive us down to the Valley. By making the requests personal, we increased our odds of being picked up, while also scoping out creeps. Win win. When I’m in charge of selecting targets I feel confident I won’t be led astray.
Who are you? And according to who?
“He was a dreamer, a thinker, a speculative philosopher… or, as his wife would have it, an idiot.”
- Douglas Adams
To a few lovely families in Yosemite, I was a creep trying to bum a ride. To actual creeps, I was sitting duck, a gift from the heavens. To the kind German family that picked me up, I was a potential interesting conversationalist for the long drive down. During the ride, the daughter practiced her English with me, and they invited me to stay with them while I studied in Europe.
When traveling, I’m often approached for directions or asked for restaurant recommendations by other foreigners, which is completely backwards. I’m the last person other tourists should request advice from because I’m equally clueless about the area. Why do people approach me? Is it because I look like I know where I’m going? No, it’s because people feel most comfortable with people that seem familiar.
When I’m considering phishing scenarios for an operation, I create an environment that I feel most comfortable with. It’s easier for me to understand and make assumptions about a topic that I know, rather than one I’m unfamiliar with. The ideal phishing candidates and context should change for each operator.
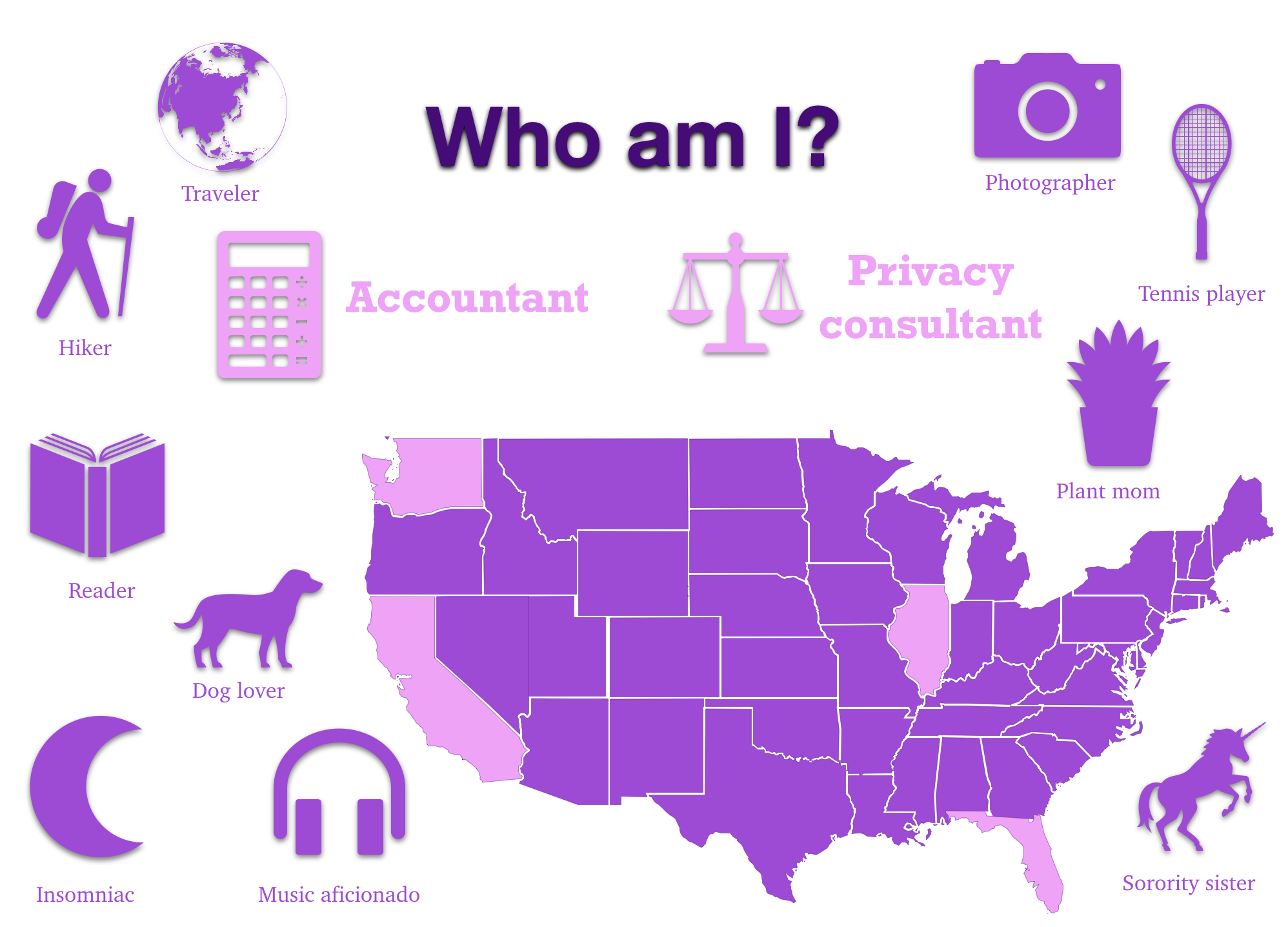
I speak lawyer. I speak accountant. I read Douglas Adams, Malcolm Gladwell, and J.K. Rowling. I play tennis. I stay up late listening to music. I travel around the world to hike in scenic spots. I use lingo from Seattle, Chicago, Miami, Prague, and the SF Bay Area… I’m dynamic (like everyone else), and I need to determine what part of me I want to leverage in my phishing campaigns.
I know my interests, so as long as the target is like me, I can assume the target’s interests. The characteristics that make me unique are the same characteristics that make me deadly for targeting and exploiting phishing candidates. What makes my phishing campaigns effective is exactly why other operators will struggle to use them as the base for their own campaigns.
For each of the potential targets listed below, I’m familiar with the culture, language, and nuances of the roles because I used to live them. I go through my old emails and use the verbiage I sent and received. It works well. Based on my life experience, my ideal phishing targets are:
1) Compliance officers and legal counsel
I led privacy projects and executed GDPR assessments. I know that organizations that adhere to EU privacy guidance create comprehensive data maps, and if I can phish a privacy officer, I get a map of the best targets across the enterprise.
Potential campaigns:
- Who am I? A fellow attorney. What am I sending to the target? A MS Word document that contains sensitive, encrypted information and can only be decrypted via a macro.
- Who am I? A concerned, confused citizen who is looking to exercising my right to be forgotten or request data. What am I sending to the target? This campaign allows for a lot of flexibility. I can send MS Word docs, PDFs, excel files, etc.
Resources I use for to develop phishing content: law360, International Association of Privacy Professionals, Google News
2) Accountants
I worked at a Big 4 accounting firm for a few years, interned in IT audit, spent two years reconciling general ledger accounts for my University, and graduated with a minor in accounting. I spent hundreds of hours validating cash flow.
Potential campaigns:
- Who am I? Treasury department representative. What am I sending to the target? A PDF of updated ledger accounts.
- Who am I? Internal audit. What am I sending to the target? Useful excel macros or EGA templates.
- Who am I? An accountant from an outside accounting firm. What am I sending to the target? A request list for items regarding a specific Financial Statement Line Item (FSLI).
Resources I use for phishing content: Microsoft Docs, Financial Accounting Standards Board, Financial Accounting textbook, Apple AppStore
Other (less ideal) phishing targets:
- Graphic designers and photographers
- Tennis players
- People living or working in Seattle, Chicago, Miami, Prague, or the San Francisco Bay Area
Embrace Nuance
When writing the phishing email, make it interesting. People love interesting. Language overcomes barriers that rational thought cannot. Language breaks down people’s abilities to make informed decisions because it encourages people to communicate interesting topics and ideas. These ideas stick with people, and to convince a target to do something, like click a link or download an executable, they need to either complete the task immediately, which can be accomplished by creating a sense of urgency, or they need to remember the task, so that they can complete it later.
Phishing Attack Vectors
What file types can we use? When is it appropriate to send these file types? What software do users have installed already that they use daily?
- Microsoft Office — Word, Excel, PowerPoint
- PDFs — Bad-Pdf, MacOS Pdf
- Images — JPEGs
- Installer packages — MacOS installer
- Browser extensions — MacOS Chrome Extensions
“Time spent wrestling with tech that does not work yet is not worth it for most, however much fun it is for nerds like us.”
— Douglas Adams
While learning how to manipulate and exploit common user functionality, I learned about Microsoft Office’s capabilities — like document generation and custom functions via JavaScript, and my life became more efficient. I wrote a macro in PowerPoint that has one purpose — standardize font type across a presentation, and I love it.
By creating useful features in a macro, the recipient’s suspicion of a document dies, and operators can hide malicious code within the macro. To create a macro, operators can use generators, such as Ghost123gg's Wep repository. There are also tools, such as Daniel Bohannon’s Invoke-Obfuscation, to hide the macro’s intentions.
Recently, @notmedic announced a new C2 (Command and Control) tool that will run completely through Excel. I’m looking forward to seeing what he comes up with. To get started with his current project, run this PowerShell script.
Trying New Ideas
See first, think later, then test. But always see first. Otherwise, you will only see what you were expecting.
- Douglas Adams
Ask yourself the following:
- Have you ever tried to watch HBO Go abroad? Did you run into some trouble with your international IP? How did you get around that?
- When was the last time you ran $pip install -r requirements.txt without checking the dependencies?
- Have you ever uploaded a .7z file to Google Drive? Did Google let you? What did you do next?
- What emails do you click on?
Many people work very hard to make the internet safe and secure, yet I do insecure things frequently. Don’t reinvent the wheel. Teach your users to bypass controls the same way you taught yourself.
A common mistake that people make when trying to design something completely foolproof is to underestimate the ingenuity of complete fools.
— Douglas Adams
The security industry reacts, and often, incident responders do not have bandwidth to work on improving a process that already works. It’s not practical to create new incident response rules before identifying viable attack vectors, which means incident response teams are vulnerable to the first attack.
So, to evade incident response teams, operators excel when being original. To cultivate creative ideas, think about real things you do. I haven’t tested out the following social engineering ideas, but here are a few examples:
- Use custom snapchat filters ($8) to phish interns with links that redirect to a malicious login site.
- Pretend to be a photographer outside of corporate building. In the afternoon, send employees their headshots in .iso format.
- Replicate emails from your real inbox as such:
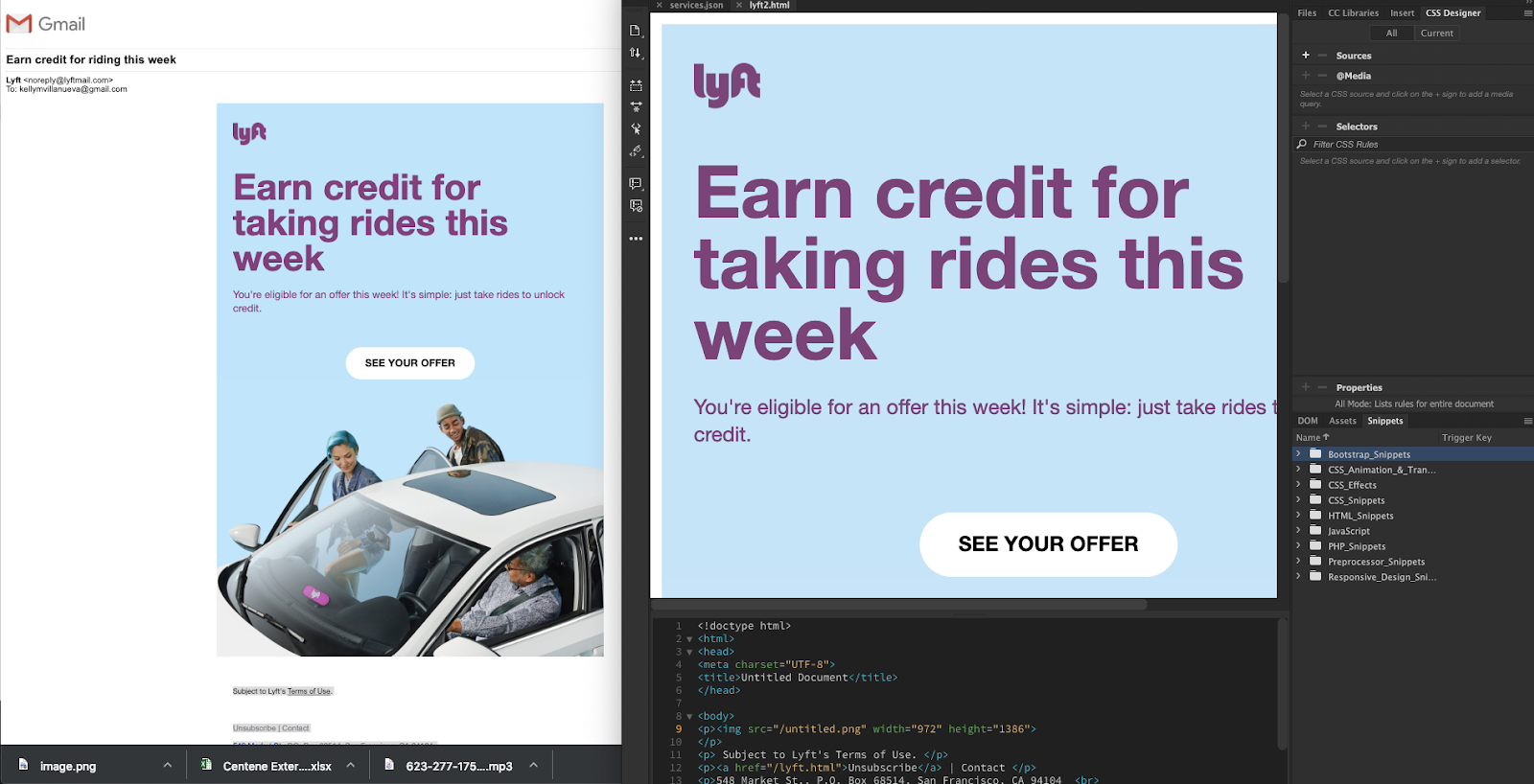
Why does this work?
Humans have a tendency to believe familiar things — people, ideas, vulnerabilities, etc. New concepts require analysis, and subconsciously, this makes people uncomfortable. Decision-making and consciousness are byproducts of evolution, and while there are many examples of why recognition and familiarity are pivotal to humanity’s development, these traits can be exploited.
Whether operators are finding phishing targets or creating phishing campaigns for unsuspecting users, usage of familiarity improves a team’s initial access capabilities and overall program maturity.
Once again, big thanks to researchers who have helped answer the “How can we gain access to a target?” question. Here are some of my favorite resources:
- Matt Nelson — SettingContent-ms Files
- Lee Christensen — Remote Code Execution via Path Traversal in the Device Metadata Authoring Wizard
- Carrie Roberts & Chevy Swanson — Phishing with Powerpoint
- Marcello Salvati — ActiveX Controls in MS Word
- Chris Ross — MacOS Chrome Extensions
Originally posted here: https://posts.specterops.io/the-hitchhikers-guide-to-initial-access-57b66aa80dd6
